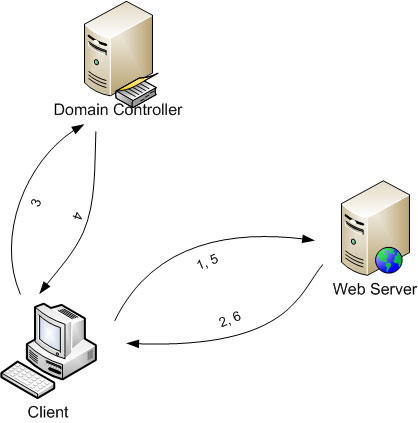
The kerberos provides a secure, single-sign-on, trusted, third party mutual authentication service. Kerberos is secure since it never transmits passwords over the network in clear.
Category: Default
Digital Signatures
Digital Signatures : A digital signature is used to authenticate the identity of the sender to the receiver to a limited extent in order to
What is Steganography?
Basically, Steganography means of transmitting the message by hiding in any file like pictures, music, movies, or any file without changing the original file format.
You need to hack!
Do you think “Why is it important?” The answer is yes it is very important because to catch a thief you must think like thief.
Algorithms and strengths
Cryptographic Algorithm Symmetric key Data Encryption Standard ( DES ) International Data Encryption Algorithm ( IDEA ) Rjindael (AES Standard ) Skipjack (used in ciphership
Cryptography
Some terms related to cryptography : Cryptography : It is the study of the mathematics techniques for all aspects of the information security. Cryptanalysis is
Getting close to BIOS
BIOS : Bios is a term that stands for the Basic Input / Output System. It consists of the low-level software that controls the system
Different types of viruses:
File infector virus: Most common form of the computer virus is the file infector virus, that hides its code within the code of the another
The cd-rom ejecting code in vb script….
Its the prank program that makes no effect with the computer hardware and software. It is just the irritating program that irritates the computer by