Building production-ready agentic AI systems on Azure AI Foundry requires proper foundation setup across your development environment, Azure infrastructure, and security configuration. This article provides
Tag: Authentication
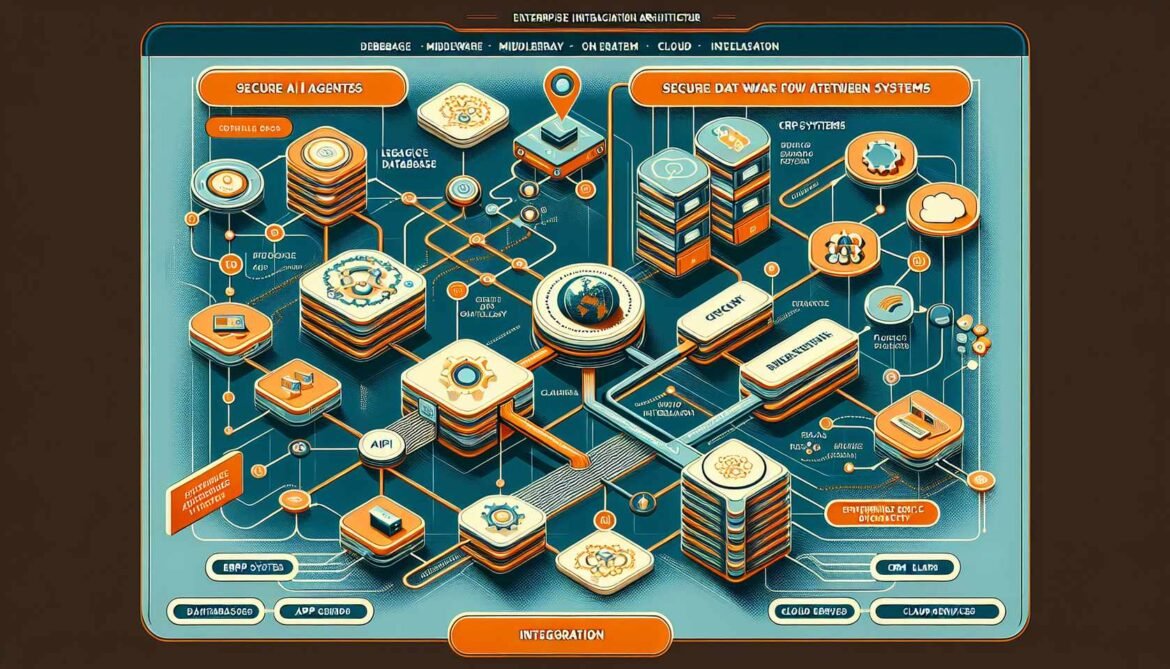
Integration with Existing Enterprise Systems for AI Agents
Connect AI agents to enterprise systems with secure integration patterns. Comprehensive guide covering database access, API integration, authentication across boundaries, transaction management, and maintaining data consistency in agent workflows.
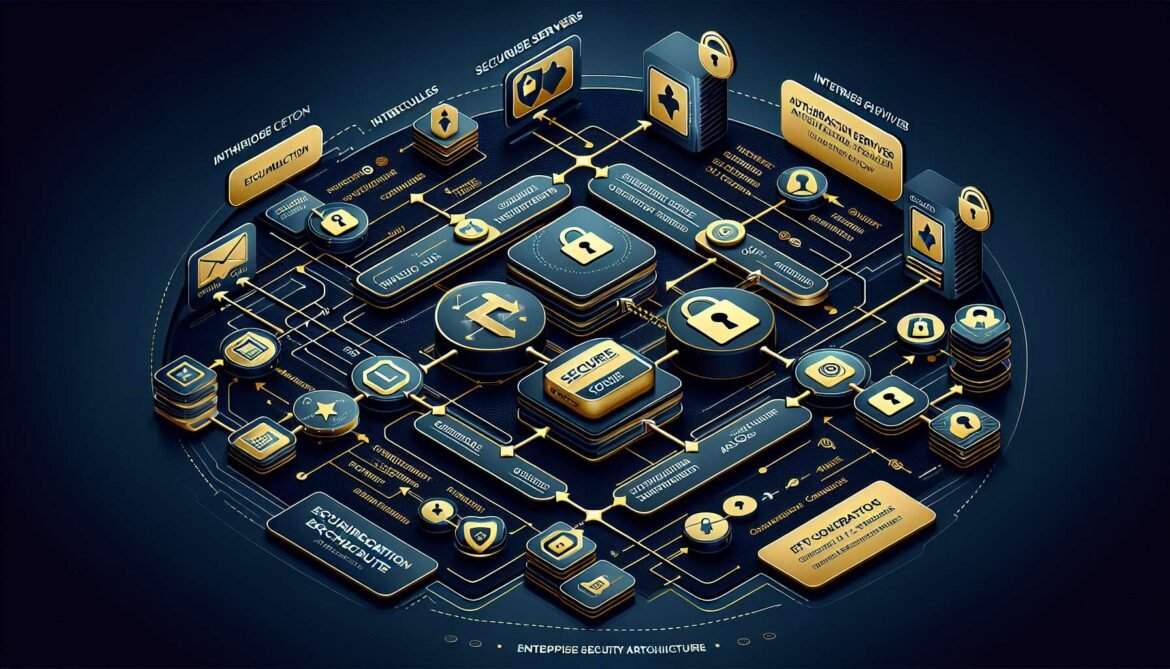
Model Context Protocol Part 4: Enterprise Integration Patterns – Security, Scaling, and Production Deployment
Master enterprise MCP integration with OAuth 2.1 authentication, role-based access control, monitoring, scaling, and security best practices. Production-ready patterns for deploying MCP servers at scale.
Real-Time WebSocket Architecture Series: Part 4 – Authentication & Security
Part 4: Comprehensive WebSocket security guide covering JWT authentication, OWASP vulnerabilities, CSRF protection, input validation, and production-ready security practices.
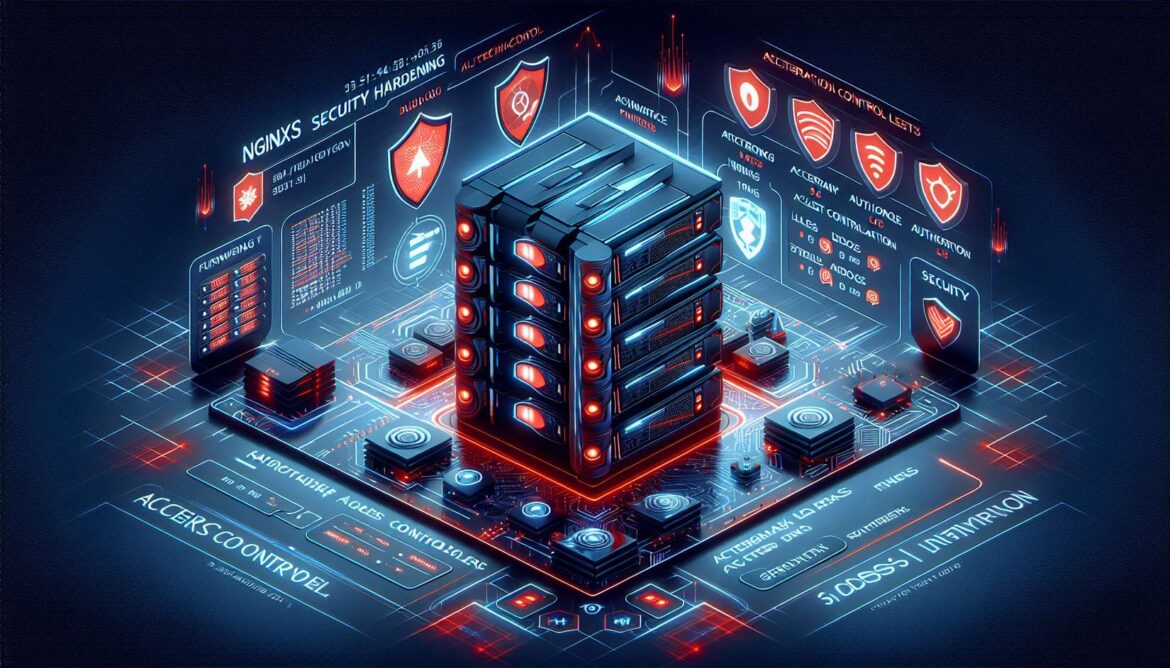
The Complete NGINX on Ubuntu Series: Part 9 – Security Hardening and Access Control
Implement comprehensive NGINX security hardening and access control on Ubuntu. Learn rate limiting, IP filtering, authentication, Fail2Ban integration, and monitoring.
MSAL Authentication in React: Complete Guide – Part 5: Advanced Topics and Production Considerations
Welcome to the final part of our MSAL authentication series! In this concluding article, we’ll cover advanced topics, production considerations, and best practices for deploying
MSAL Authentication in React: Complete Guide – Part 4: Token Management and API Calls
Welcome to Part 4 of our MSAL authentication series! Now that we have protected routes in place, let’s dive into token management and making authenticated
MSAL Authentication in React: Complete Guide – Part 3: Protected Routes and Route Guards
Welcome to Part 3 of our MSAL authentication series! Now that we have our authentication provider set up, let’s implement protected routes and route guards
MSAL Authentication in React: Complete Guide – Part 2: MSAL Provider and Authentication Context
Welcome back to our MSAL authentication series! In Part 1, we covered the basics of MSAL and Azure AD setup. Now, let’s implement the MSAL
MSAL Authentication in React: Complete Guide – Part 1: Introduction and Setup
Microsoft Authentication Library (MSAL) provides robust authentication capabilities for React applications, enabling seamless integration with Azure Active Directory and Microsoft Identity Platform. In this comprehensive