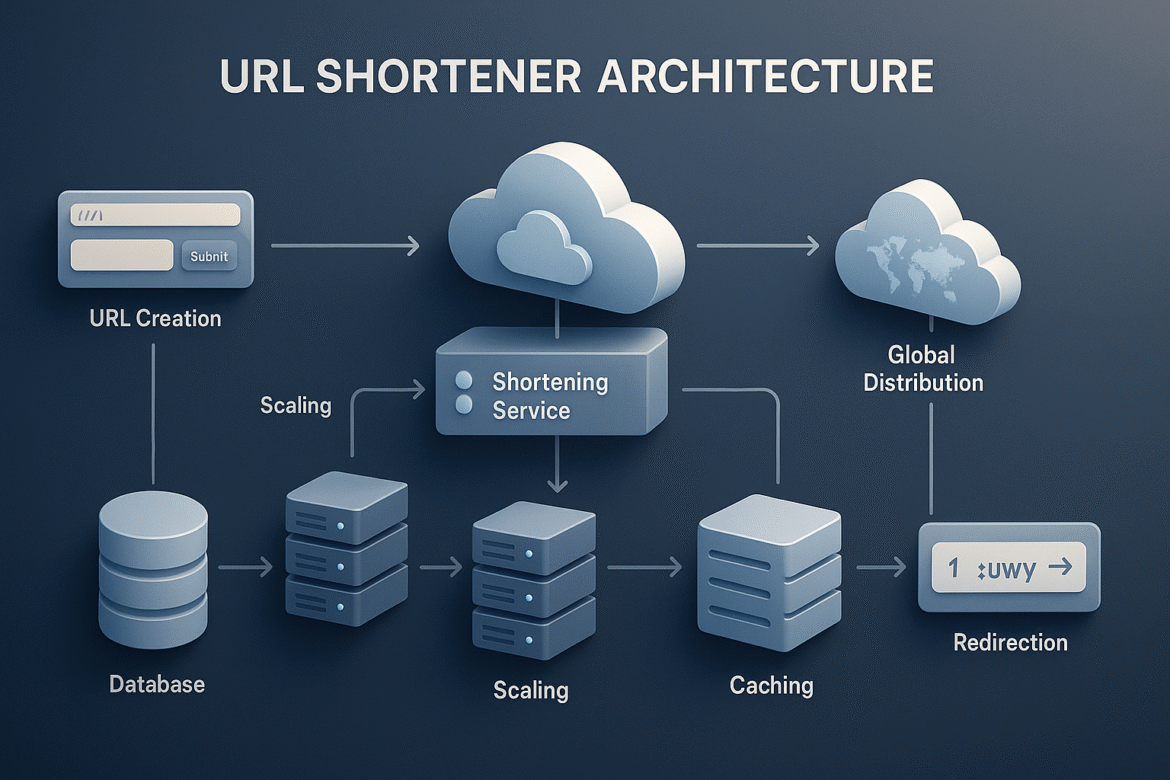
Building a URL shortener that handles 100 million URLs per day teaches fundamental lessons about cloud architecture, distributed systems, and Azure services. This series explores every architectural decision needed to build production-ready systems at scale.
Author: Chandan
How to Deploy Your Apps Using Azure Bicep
Learn how to deploy Node.js applications to Azure using Bicep and Azure Developer CLI (azd). This comprehensive guide covers everything from setup to production deployment with PostgreSQL, including practical code examples and troubleshooting tips.
Sharpening Your Mind: A Practical Guide to Enhancing Critical Thinking
Learn practical techniques to enhance your critical thinking skills with real-world examples and step-by-step exercises. From questioning assumptions to structured problem-solving, discover how to make better decisions in both personal and professional contexts.
Artificial Intelligence and Its Future: Navigating Tomorrow’s Digital Landscape
Explore the current state of artificial intelligence and discover what the future holds for AI technology. From emerging trends and industry applications to challenges and preparations needed for an AI-driven world.
Unlocking the Power of Durable Azure Functions: Real-World Use Cases for Modern Applications
Discover how Durable Azure Functions enable stateful serverless computing for complex workflows. Learn practical use cases from e-commerce order processing to IoT device management, plus implementation best practices.
Data Security in MCP Server: Essential Practices for Developers
Explore essential security practices for MCP servers, covering authentication, encryption, data handling, and compliance requirements for AI applications.
Building Reliable Workflows with Azure Durable Functions
Azure Durable Functions represent a powerful extension of Azure Functions that enables developers to build stateful functions in a serverless compute environment. Unlike traditional Azure
Tips for managing and leading a software development team effectively
A comprehensive guide covering essential strategies for managing software development teams, including communication, processes, technical decision-making, and team culture.
Developing Secure Software Applications in the Age of Cyber Threats
Learn essential practices for developing secure software applications in today’s threat landscape. This comprehensive guide covers security principles, secure coding practices, and strategies to protect against modern cyber threats.
Best practices for integrating third-party APIs and services into your software
Master the art of third-party API integration with this comprehensive guide covering planning, security, implementation strategies, error handling, and best practices for reliable service integration.