- Why Building a URL Shortener Taught Me Everything About Cloud Architecture
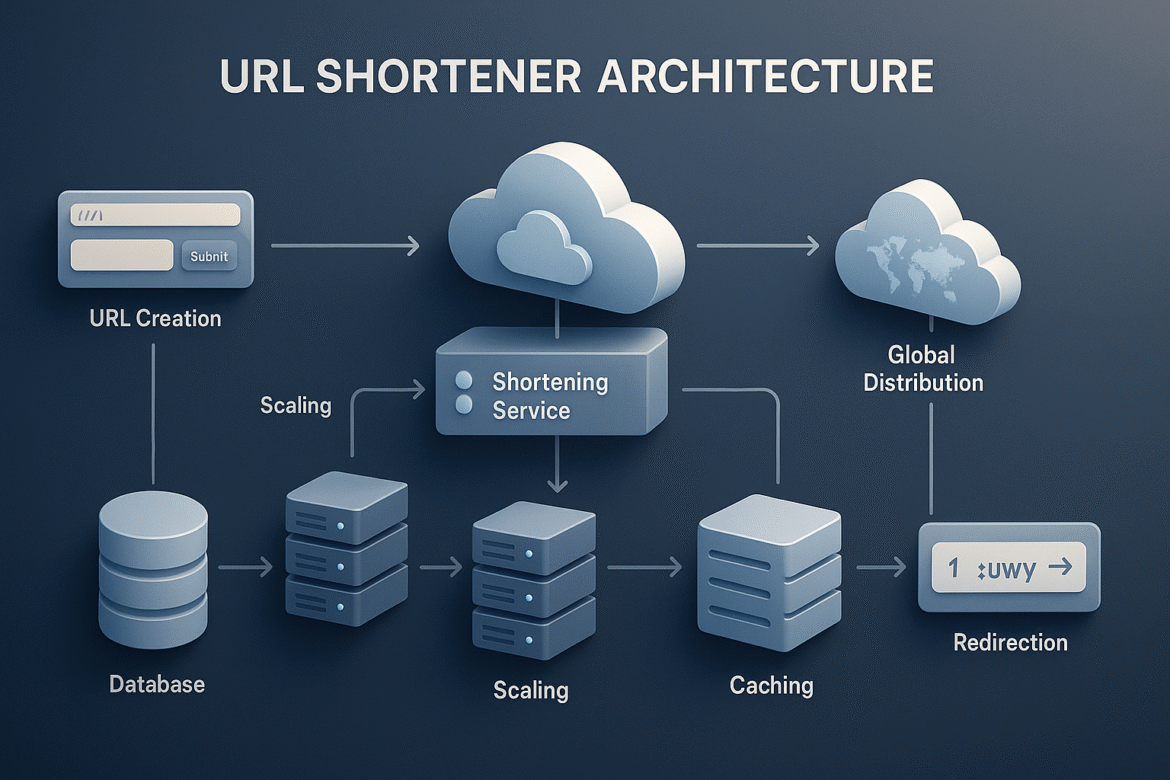
- From Napkin Sketch to Azure Blueprint: Designing Your URL Shortener’s Foundation
- From Architecture to Implementation: Building the Engine of Scale
- Analytics at Scale: Turning Millions of Click Events Into Intelligence
- Security and Compliance at Scale: Building Fortress-Grade Protection Without Sacrificing Performance
- Performance Optimization and Cost Management: Engineering Excellence at Sustainable Economics
- Monitoring, Observability, and Operational Excellence: Building Systems That Tell Their Own Story
- Deployment, DevOps, and Continuous Integration: Delivering Excellence at Scale
Part 5 of the “Building a Scalable URL Shortener on Azure” series
In our previous post, we built a sophisticated analytics system that processes millions of click events per second, transforming raw data streams into actionable intelligence through event-driven architectures. We explored how Azure Event Hubs, Stream Analytics, and real-time dashboards work together to provide immediate insights without impacting core system performance.
Now we face one of the most challenging aspects of building production systems: implementing comprehensive security that protects against sophisticated threats while maintaining the blazing-fast performance characteristics our users have come to expect. This challenge becomes exponentially more complex when you’re operating at scale, where traditional security approaches can become bottlenecks that cripple system performance.
Today, we’re going to explore how security architecture must be woven into every layer of our system from the very beginning, rather than bolted on as an afterthought. Think of this as designing a fortress that can withstand coordinated attacks while allowing millions of legitimate users to flow through seamlessly. The architectural patterns we’ll develop teach fundamental principles that apply to any system where security and performance must coexist harmoniously.
Understanding security at scale requires shifting your mental model from thinking about individual threats to thinking about threat patterns, attack vectors, and the emergent behaviors that arise when malicious actors target systems processing millions of requests. The techniques we’ll explore today protect everything from financial trading platforms to social media networks to critical infrastructure systems.
The key insight that transforms how you approach security architecture is recognizing that security cannot be a single point of failure or a performance bottleneck. Instead, security must be distributed across every component, working in concert to create defense-in-depth that becomes stronger under pressure rather than weaker.
The Security Challenge: Protection Without Performance Penalty
Before diving into Azure’s security services and implementation details, we need to understand why security at our scale requires fundamentally different thinking than traditional enterprise security approaches. The challenge lies in balancing seemingly opposing forces: the need for comprehensive protection against sophisticated threats, and the requirement for sub-millisecond response times that users expect from modern applications.
Traditional security approaches often work by creating checkpoints where every request gets thoroughly examined before being allowed to proceed. This approach works well for lower-volume systems, but creates catastrophic bottlenecks when you’re processing millions of requests per second. Imagine trying to inspect every car at a highway checkpoint during rush hour – the traffic backup would extend for miles, defeating the purpose of having a highway in the first place.
The solution requires thinking about security as a continuous process rather than a series of gates. Instead of stopping every request for inspection, we implement intelligent monitoring that observes patterns and behaviors, flagging anomalies for deeper investigation while allowing normal traffic to flow unimpeded. This approach, called behavioral security, enables us to detect sophisticated attacks that might bypass traditional rule-based systems while maintaining the performance characteristics our users demand.
Consider what happens when our URL shortener faces a distributed denial-of-service attack where thousands of compromised machines attempt to overwhelm our system with malicious requests. Traditional security approaches might try to analyze each request individually, quickly becoming overwhelmed by the sheer volume. Our approach will instead look for patterns in request behavior, geographic distribution, and timing that indicate coordinated attacks, automatically implementing countermeasures that preserve service for legitimate users while mitigating the attack.
Understanding this shift from reactive security to proactive pattern recognition forms the foundation for everything we’ll build in this exploration. We’re not just protecting against known threats – we’re building systems that can adapt and respond to novel attack patterns as they emerge.
Azure Security Architecture: Building Defense in Depth
Azure provides a comprehensive security ecosystem that enables us to implement sophisticated protection at every layer of our architecture. The elegance of Azure’s approach lies in how these services integrate seamlessly with each other and with our application components, creating a security fabric that strengthens the entire system without introducing performance penalties.
Understanding how to orchestrate Azure’s security services requires thinking about security boundaries and trust relationships. Each component in our system operates within defined security boundaries, with carefully controlled pathways for communication between components. This approach, called zero-trust architecture, assumes that threats can emerge from anywhere and verifies every interaction rather than trusting based on network location or component identity alone.
The foundation of our security architecture rests on Azure Active Directory, which provides identity and access management capabilities that scale to millions of users while maintaining single-sign-on convenience. But AAD is far more than a user directory – it’s an intelligent identity platform that uses machine learning to detect unusual sign-in patterns, impossible travel scenarios, and other indicators of compromised accounts.
Building on this identity foundation, we layer additional security services that each address specific aspects of the threat landscape. Azure Key Vault protects cryptographic keys and secrets, ensuring that sensitive configuration data never appears in our application code or deployment pipelines. Azure Security Center provides continuous security monitoring and recommendations, using machine learning to identify misconfigurations and potential vulnerabilities before they can be exploited.
The key insight that ties these services together is understanding how they create emergent security properties that exceed the sum of their individual capabilities. When Azure Sentinel analyzes security events from multiple sources, it can detect attack patterns that would be invisible to any single security component. This holistic approach to security monitoring becomes our early warning system for sophisticated threats.
/// <summary>
/// Comprehensive security service that integrates multiple Azure security components
/// This implementation demonstrates how to build layered security without impacting performance
/// </summary>
public class IntegratedSecurityService : ISecurityService
{
private readonly IKeyVaultService _keyVault;
private readonly IThreatDetectionService _threatDetection;
private readonly IAuditService _auditService;
private readonly IComplianceService _complianceService;
private readonly ILogger<IntegratedSecurityService> _logger;
private readonly SecurityConfiguration _config;
// High-performance threat detection using in-memory patterns
private readonly ConcurrentDictionary<string, ThreatProfile> _activeThreatProfiles;
private readonly RateLimitingService _rateLimiter;
private readonly GeofencingService _geofencing;
public IntegratedSecurityService(
IKeyVaultService keyVault,
IThreatDetectionService threatDetection,
IAuditService auditService,
IComplianceService complianceService,
ILogger<IntegratedSecurityService> logger,
IOptions<SecurityConfiguration> config)
{
_keyVault = keyVault;
_threatDetection = threatDetection;
_auditService = auditService;
_complianceService = complianceService;
_logger = logger;
_config = config.Value;
_activeThreatProfiles = new ConcurrentDictionary<string, ThreatProfile>();
_rateLimiter = new RateLimitingService(config);
_geofencing = new GeofencingService(config);
}
/// <summary>
/// Validates incoming requests using multi-layered security analysis
/// This method demonstrates how to implement comprehensive security checking
/// without introducing latency that impacts user experience
/// </summary>
public async Task<SecurityValidationResult> ValidateRequestAsync(
HttpRequest request,
string shortCode = null)
{
var stopwatch = Stopwatch.StartNew();
var validationContext = CreateValidationContext(request, shortCode);
try
{
// Layer 1: Fast path validation for obviously legitimate requests
// This layer handles the majority of requests with minimal overhead
var quickValidation = await PerformQuickValidationAsync(validationContext);
if (quickValidation.IsDefinitivelyValid)
{
await LogSecurityEventAsync(SecurityEventType.QuickValidationPassed, validationContext);
return SecurityValidationResult.Allow(quickValidation.TrustScore);
}
// Layer 2: Enhanced validation for suspicious but not obviously malicious requests
// This layer performs deeper analysis while maintaining acceptable performance
var enhancedValidation = await PerformEnhancedValidationAsync(validationContext);
if (enhancedValidation.IsBlocked)
{
await LogSecurityEventAsync(SecurityEventType.EnhancedValidationBlocked, validationContext);
return SecurityValidationResult.Block(enhancedValidation.ThreatScore, enhancedValidation.Reason);
}
// Layer 3: Deep analysis for highly suspicious requests
// This layer may introduce some latency but provides comprehensive protection
if (enhancedValidation.RequiresDeepAnalysis)
{
var deepValidation = await PerformDeepValidationAsync(validationContext);
await LogSecurityEventAsync(SecurityEventType.DeepValidationCompleted, validationContext);
return deepValidation.IsBlocked
? SecurityValidationResult.Block(deepValidation.ThreatScore, deepValidation.Reason)
: SecurityValidationResult.Allow(deepValidation.TrustScore);
}
// Default to allowing the request with monitoring
await LogSecurityEventAsync(SecurityEventType.DefaultAllow, validationContext);
return SecurityValidationResult.Allow(enhancedValidation.TrustScore);
}
catch (Exception ex)
{
// Security validation failures should never block legitimate users
// We log the error and default to allowing the request with additional monitoring
_logger.LogError(ex, "Security validation failed for request {RequestId}", validationContext.RequestId);
await LogSecurityEventAsync(SecurityEventType.ValidationError, validationContext, ex);
return SecurityValidationResult.Allow(0.5, "Security validation error - allowing with monitoring");
}
finally
{
// Track performance metrics to ensure security doesn't impact user experience
var duration = stopwatch.Elapsed;
_telemetry.TrackSecurityValidationPerformance(duration, validationContext.RequestType);
if (duration.TotalMilliseconds > _config.PerformanceWarningThresholdMs)
{
_logger.LogWarning("Security validation took {Duration}ms for request {RequestId}",
duration.TotalMilliseconds, validationContext.RequestId);
}
}
}This security service implementation demonstrates how to build comprehensive protection that scales with your system rather than becoming a bottleneck. The layered validation approach ensures that the vast majority of legitimate requests flow through quickly, while suspicious requests receive the deeper analysis they warrant. The key insight here is that security and performance are not opposing forces – they can work together when properly architected.
Threat Detection and Response: Building Intelligent Protection
Moving beyond basic validation, we need sophisticated threat detection capabilities that can identify emerging attack patterns and coordinate automated responses across our entire infrastructure. This requires building systems that learn from attack patterns and adapt their defensive strategies accordingly, creating an intelligent security layer that becomes more effective over time.
Understanding behavioral threat detection requires shifting from rule-based thinking to pattern-based thinking. Instead of trying to anticipate every possible attack vector and create rules to block them, we observe normal system behavior and flag deviations that indicate potential threats. This approach enables us to detect novel attacks that have never been seen before, including zero-day exploits and sophisticated targeted attacks.
The challenge in building effective threat detection lies in balancing sensitivity with false positive rates. Too sensitive, and legitimate users get blocked or challenged unnecessarily. Too permissive, and real threats slip through undetected. The solution involves building confidence models that correlate multiple indicators rather than relying on any single signal.
/// <summary>
/// Analyzes temporal patterns in click events to detect automated behavior
/// Human clicking patterns have natural randomness, while automated systems show regularity
/// </summary>
private TemporalAnalysisResult AnalyzeTemporalPatterns(List<ClickEvent> clicks)
{
if (clicks.Count < 10)
{
// Insufficient data for reliable temporal analysis
return new TemporalAnalysisResult
{
ThreatScore = 0.0,
Confidence = 0.3,
Features = new Dictionary<string, double>(),
Indicators = new[] { "Insufficient data for temporal analysis" }
};
}
// Sort clicks by timestamp for time series analysis
var sortedClicks = clicks.OrderBy(c => c.Timestamp).ToList();
// Calculate inter-click intervals
var intervals = new List<double>();
for (int i = 1; i < sortedClicks.Count; i++)
{
var interval = (sortedClicks[i].Timestamp - sortedClicks[i - 1].Timestamp).TotalMilliseconds;
intervals.Add(interval);
}
// Analyze interval statistics
var meanInterval = intervals.Average();
var intervalVariance = intervals.Sum(i => Math.Pow(i - meanInterval, 2)) / intervals.Count;
var intervalStdDev = Math.Sqrt(intervalVariance);
var coefficientOfVariation = intervalStdDev / meanInterval;
// Detect periodic patterns that indicate automation
var periodicity = DetectPeriodicity(intervals);
// Analyze burst patterns - sudden spikes in activity
var burstAnalysis = AnalyzeBurstPatterns(sortedClicks);
// Calculate threat score based on temporal characteristics
var threatScore = 0.0;
var indicators = new List<string>();
// Low coefficient of variation suggests regular, non-human patterns
if (coefficientOfVariation < 0.3)
{
threatScore += 0.4;
indicators.Add("Highly regular click intervals detected");
}
// Strong periodicity suggests automated clicking
if (periodicity.Strength > 0.7)
{
threatScore += 0.5;
indicators.Add($"Strong periodic pattern detected (period: {periodicity.Period}ms)");
}
// Unusual burst patterns can indicate coordinated attacks
if (burstAnalysis.HasAnomalousBursts)
{
threatScore += 0.3;
indicators.Add($"Anomalous burst patterns detected ({burstAnalysis.BurstCount} bursts)");
}
// Very fast clicking suggests automation
if (meanInterval < 100) // Less than 100ms between clicks
{
threatScore += 0.6;
indicators.Add($"Suspiciously fast clicking detected (mean interval: {meanInterval:F1}ms)");
}
return new TemporalAnalysisResult
{
ThreatScore = Math.Min(threatScore, 1.0),
Confidence = CalculateTemporalAnalysisConfidence(intervals.Count, intervalVariance),
Features = new Dictionary<string, double>
{
["MeanInterval"] = meanInterval,
["IntervalVariance"] = intervalVariance,
["CoefficientOfVariation"] = coefficientOfVariation,
["PeriodicityStrength"] = periodicity.Strength,
["BurstCount"] = burstAnalysis.BurstCount
},
Indicators = indicators
};
}This threat detection implementation demonstrates how to build intelligent security systems that learn and adapt rather than simply following static rules. The temporal analysis capabilities can detect subtle patterns that indicate automated behavior, while the coordinated response system ensures that threats are addressed quickly and proportionally.
Understanding the principles demonstrated here – behavioral analysis, pattern recognition, and adaptive response – provides the foundation for protecting any high-scale system against sophisticated threats. These techniques scale naturally with your system, becoming more effective as they observe more behavior patterns and encounter more varied attack scenarios.
Compliance and Audit Trails: Building Trust at Scale
Beyond protecting against active threats, modern systems must also demonstrate compliance with regulatory requirements and provide comprehensive audit trails that satisfy enterprise governance requirements. This becomes particularly challenging at scale, where traditional compliance approaches can generate overwhelming amounts of data while failing to provide the actionable insights that auditors and compliance teams actually need.
The key insight for building effective compliance systems is recognizing that compliance is not just about logging every action – it’s about creating verifiable evidence that your system operates according to defined policies and procedures. This requires thinking about compliance data as a first-class concern in your architecture, not an afterthought that gets bolted on later.
Our compliance architecture must balance several competing requirements: comprehensive coverage of all security-relevant events, efficient storage and retrieval of audit data, real-time alerting for compliance violations, and the ability to generate compliance reports that satisfy various regulatory frameworks without manual intervention.
The Complete Security Architecture: Integration and Resilience
Throughout this exploration of security at scale, we’ve built a comprehensive protection system that demonstrates how security and performance can work together rather than against each other. The layered approach we’ve implemented creates defense-in-depth that becomes stronger under pressure, while the behavioral analysis capabilities enable detection of sophisticated threats that would bypass traditional rule-based systems.
The integration between Azure’s security services, our custom threat detection logic, and the compliance framework creates a security ecosystem that provides value at multiple levels. Security operations teams get immediate alerting and automated response capabilities. Compliance teams get comprehensive audit trails and automated reporting. Development teams get security capabilities that integrate seamlessly with their existing workflows without introducing performance penalties.
Most importantly, this security architecture scales naturally with your system growth. The pattern recognition capabilities become more accurate as they observe more behavior. The automated response systems become more sophisticated as they encounter more varied attack scenarios. The compliance frameworks become more comprehensive as they capture more diverse operational patterns.
Coming Up in Part 6: “Performance Optimization and Cost Management”
In our next installment, we’ll explore the critical balance between system performance and operational costs that determines the long-term success of high-scale applications. We’ll dive into Azure’s cost optimization tools, implement intelligent auto-scaling strategies, and design monitoring systems that help you optimize for both performance and cost efficiency.
We’ll discover how performance optimization and cost management are not opposing forces but complementary strategies that reinforce each other when properly implemented. The techniques we’ll explore help you deliver exceptional user experiences while maintaining sustainable operational economics.
This is Part 5 of our 8-part series on building scalable systems with Azure. Each post builds upon previous concepts while exploring the sophisticated security implementations that protect modern applications serving millions of users.
Series Navigation:
← Part 4: Analytics at Scale
→ Part 6: Performance Optimization and Cost Management – Coming Next Week






One thought on “Security and Compliance at Scale: Building Fortress-Grade Protection Without Sacrificing Performance”
Comments are closed.